- Traditional Authentication
- Get to Know Your Users With Mobile Identity Services
- Streamline Digital Interactions
- Comply With Strict Regulations
- Protect Yourself and Customers From Fraud
- Embracing Next Generation Verification Methods for a Secure Digital Future
With cybercrime on the rise and rules and regulations getting (rightfully) stricter each year, it's important that you as a business keep up with the pace of online security. Traditionally, a lot of organizations apply multi- or two-factor authentication (MFA or 2FA) to secure accounts and data. And for a lot of cases, that's absolutely fine!
Traditional Authentication
Two-factor authentication or 2FA often utilizes One Time Passwords (OTPs) as a verification tool. A user logs in with a password, and a temporary password or code will be sent to a different channel for verification. This code is then entered into the digital environment and it will grant the user access.
But what does this method truly verify? Authentication via OTP proves that the user is in possession of the phone, email address, or socials account that the OTP is sent to. Nothing more, nothing less. And that can be a perfect way to secure online accounts, because it checks whether a user is allowed to have access to an account or not, but it doesn't check the actual identity of the user. But what if there are more specific requirements? Can you, as a business, truly KNOW who's on the other end of the internet, trying to access your digital services or transactions? Is there a more in-depth way of verifying your users?
Get to Know Your Users With Mobile Identity Services
With Mobile Identity Services, your can authenticate users, verify identities, and prevent fraud by using the SIM card and mobile network operator data. This will compare and match user data to the (live) data that telecom operators have - ensuring that you as a business will actually KNOW and VERIFY who's trying to access your online services. This will help secure all digital interactions between you and your customers, and it means that you'll stay compliant with strict (international) data protection and user authentication regulations.
Mobile Identity Services offers several sub-services that can each provide their own unique added benefits for your business, called Number Verify, Identity Match, and Takeover Protection. We'll highlight these services below.
Streamline Digital Interactions
Number Verify can improve user satisfaction and security, while also streamlining operational processes. It is a verification method that leverages the unique characteristics of the SIM card to silently verify users that try to log into your app. Users only need to enter their telephone number and the verification will then happen between the mobile operator data and the SIM card. This results in a quick and user-friendly login process, as users no longer need to remember passwords or wait for and copy one time passwords. And because the SIM card is inherently secure and difficult to tamper with, it's also considered safer than traditional verification methods. Imagine the following scenario:
A customer, Emma, loses access to her mobile banking app because she forgot her password. Instead of navigating through a lengthy password recovery process, she opts for the app's "Login with Phone Number" option powered by Number Verify. She enters her phone number, and the silent verification in the background quickly lets her log into her account.
Thanks to Number Verify, Emma was able to have a seamless user experience, rather than going through the complex password reset flow and possibly wait for OTPs to be delivered. Fewer password recovery issues also relieve some pressure on your support teams, as they'll have to deal with fewer calls and emails regarding this topic.
Read all about Number Verify >>
Comply With Strict Regulations
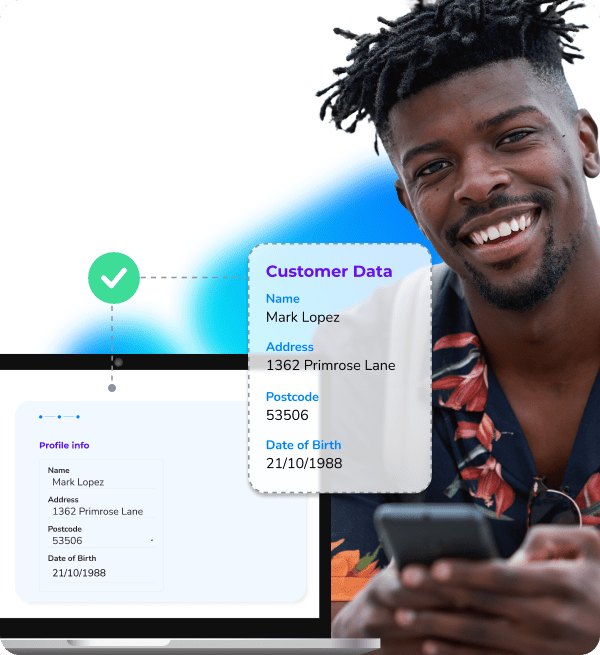
Identity Match utilizes the mobile number of a user to verify their name, address, postcode, and date of birth against live data from their mobile network operator. This will allow you to confirm mobile number ownership using first-party data while ensuring privacy through hashing and compliance with consent guidelines like GDPR.
So, in practice, what is the added benefit of checking so many personal details via SIM card data? Well, one example is age restrictions. Certain industries and businesses need to comply with strict age verification requirements - like financial services or the entertainment industry.
High-stakes financial businesses often need to adhere to strict GDPR and KYC (Know Your Customers) guidelines - they NEED to verify the applicants identity before creating new bank accounts, offering them loans, or allowing them to partake in gambling. Imagine the following scenario:
Emma, back again for a new adventure, wants to apply for a loan as a potential new customer. She fills out an online application and provides her mobile phone number. Before proceeding, Emma is prompted to consent to the use of her personal details (name, address, date of birth) in compliance with GDPR. If she agrees, the Identity Match will check her data directly with the mobile network operator and allow her to continue the sign-up.
Within seconds, Emma’s details are matched and confirmed as correct, which streamlines the whole process while staying compliant with strict guidelines and mitigating the risk of identity fraud.
Protect Yourself and Customers From Fraud
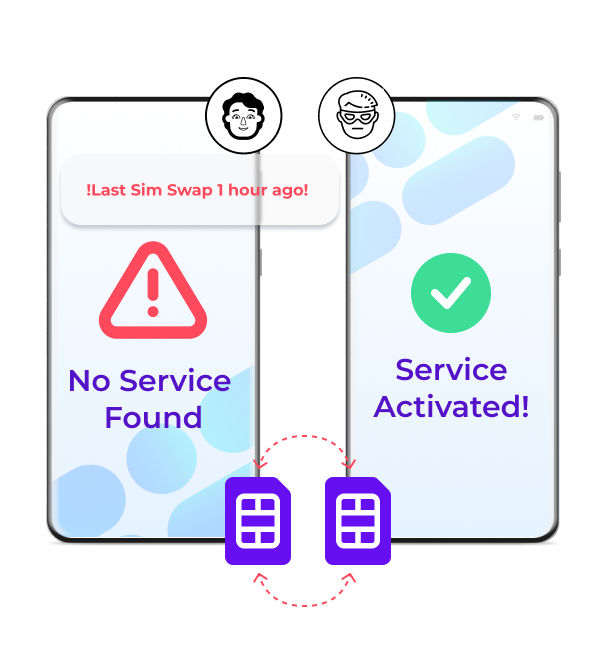 Using SIM card data to verify users is more secure than other verification methods, but what if criminals manage to commit SIM swap fraud? SIM Swap fraud happens when criminals manage to persuade mobile carriers to transfer the telephone number of a victim to a SIM card in their possession, giving them access to sensitive information such as text messages and phone calls.
Using SIM card data to verify users is more secure than other verification methods, but what if criminals manage to commit SIM swap fraud? SIM Swap fraud happens when criminals manage to persuade mobile carriers to transfer the telephone number of a victim to a SIM card in their possession, giving them access to sensitive information such as text messages and phone calls.
Well, to prevent SIM swap fraudsters from succeeding, Mobile Identity Services also offer Takeover Protection - an additional service that detects SIM card changes and flags them as potential fraud. This puts you in control of determining the next steps with that particular SIM card and/or user.
Takeover Protection identifies the SIM swap before fraudsters can intercept sensitive communications, preventing unauthorized transactions. Imagine this scenario:
A long-time customer of your financial business, Emma, initiates a large bank transfer via the bank's mobile app. But is it really Emma? Unbeknownst to her, her mobile number has recently been compromised through a SIM swap fraud attempt. Criminals plan to intercept the OTP required to authorize the transfer to try and steal the money. Luckily, when the transaction is requested, your Takeover Protection service flags her number as high-risk because the SIM card was recently swapped. The transaction is paused and a secondary verification is requested. Emma, now aware of the issue, contacts you to inform you of her comprised account and then you can take the next steps together.
Critical transactions like money transfers are safeguarded, ensuring both the bank and the customer avoid financial losses. This in turn will also build trust between you and your customers.
Embracing Next Generation Verification Methods for a Secure Digital Future
In a rapidly evolving digital landscape, where cybercrime is becoming increasingly sophisticated and regulations more strict, businesses must prioritize secure, user-friendly, and compliant verification methods. Traditional methods like passwords and OTPs have served well, but they can fall short when it comes to newer cyber threats or increased security guidelines - criminals are crafty and with every technological innovation, they will try to abuse it.
Mobile Identity Services offer a user-friendly and more secure method of verification by leveraging the inherently secure SIM card data and real-time mobile network operator information. Services such as Number Verify, Identity Match, and Takeover Protection not only enhance security but also streamline user experiences, ensuring compliance with international regulations like GDPR. From enabling seamless logins with Number Verify to safeguarding high-value transactions with Takeover Protection, these verification solutions will help you truly get to KNOW who's on the other end of the internet - or who isn't.
Protect yourself and your customers from evolving threats, build trust, and stay compliant. The future of secure and compliant digital interactions starts with Mobile Identity Services.
