Mobile Identity leverages the unique characteristics of the SIM card to authorise and verify users. This provides a secure authorisation, verification, and fraud prevention method that ensures only authorised users can access sensitive information.
By using the unique properties of the SIM card, which are difficult to tamper with, Mobile Identity verifications ensure a higher level of security compared to traditional methods.
Users do not need to remember complex passwords, look for tokens, or carry additional authentication devices. The mobile phone becomes the key to access.
Detect and prevent account takeover scams such as SIM Swap fraud by checking when the last SIM swap took place.
Lower your operational costs by reducing the need for physical tokens and complex password management systems.
A new, quick and secure verification channel: Number Verify. Users only need to fill out their phone number, and the verification itself will happen in the background between mobile operators and the SIM card of the customer's phone. This makes it more safe and secure than traditional authentication methods that rely on passwords, knowledge-based authentication, physical tokens, or OTPs.
Verify users silently in the background
Simplify the authentication process
Reduce fraud
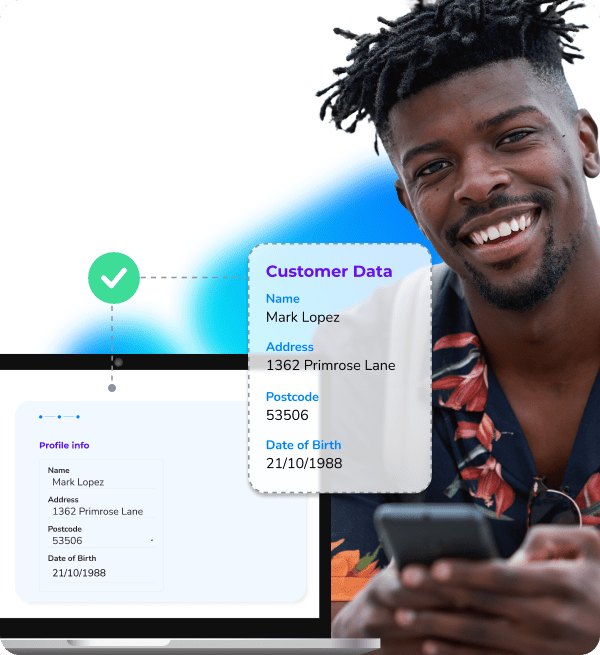
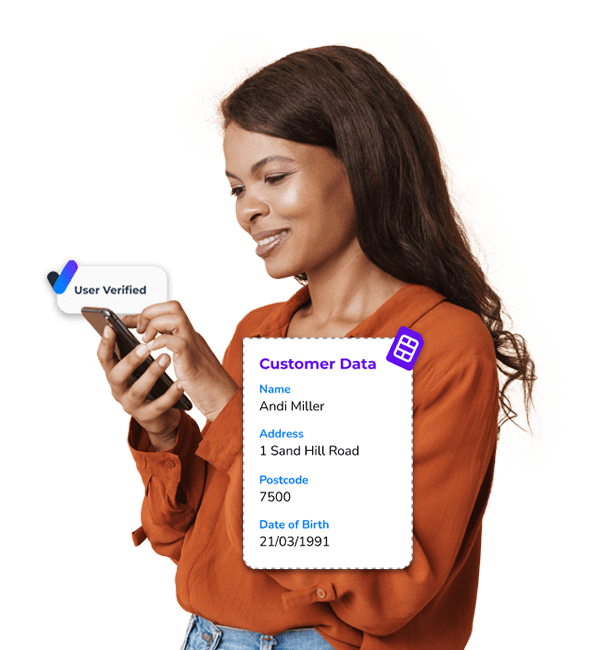
Identity Match uses a customer's mobile number to verify their name, address, postcode, and date of birth against live data from their mobile network operator. This allows businesses to confirm mobile number ownership using first-party data while ensuring privacy through hashing and compliance with consent guidelines like GDPR.
Verify customer data
Anti Money Laundering (AML) policies
Grow your database by verifying more users securely
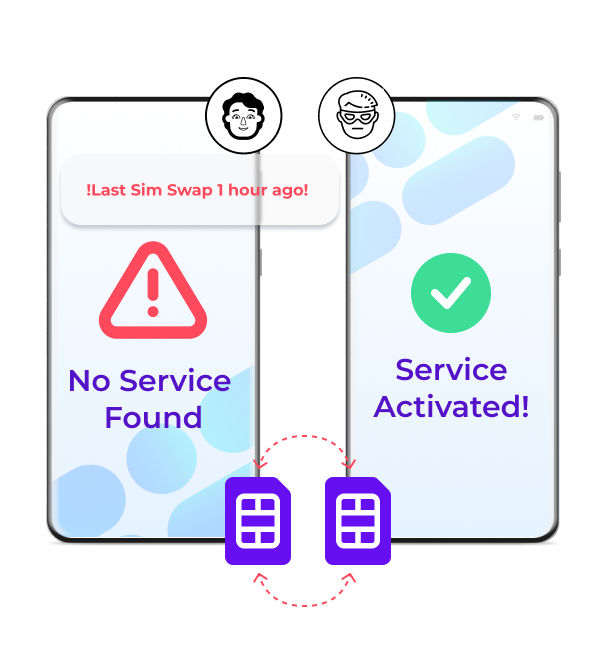
SIM Swap fraud occurs when fraudsters manage to persuade mobile carriers to transfer the telephone number of a victim to a SIM card in their possession, giving them access to sensitive information such as text messages and phone calls. Our Takeover Protection Service determines when a SIM card was changed and will flag it as potential fraud. This will put you in charge of the situation and help prevent this fraud.
Use real-time data
Set up fraud alarms and signals
Stay in control
Onboard and grant access to users in a smooth and secure manner
Protect data or monetary transactions from fraudsters
Monitor logins to online data and accounts to prevent unauthorised access
Double-check users by confirming their mobile numbers
Comply with strict data protection and user authentication regulations.
One API, multiple OTP channels. Choose the perfect channels for your audience and improve the user experience.
One API for the most secure and user friendly verification services including OTPs and Number Verify. Only pay per successful verification.
Build and configure your own tailored verification and security solution with multiple channels to perfectly fit existing processes.
With cybercrime on the rise, it's more important than ever to secure your online data and customers - if you don't want to become the next security breach headline.
With our Mobile Identity services supported by Sekura.id, you'll stay on top of international security regulations whilst offering your customers the highest level of security that is also user-friendly to boost.
Select a region to show relevant information. This may change the language.