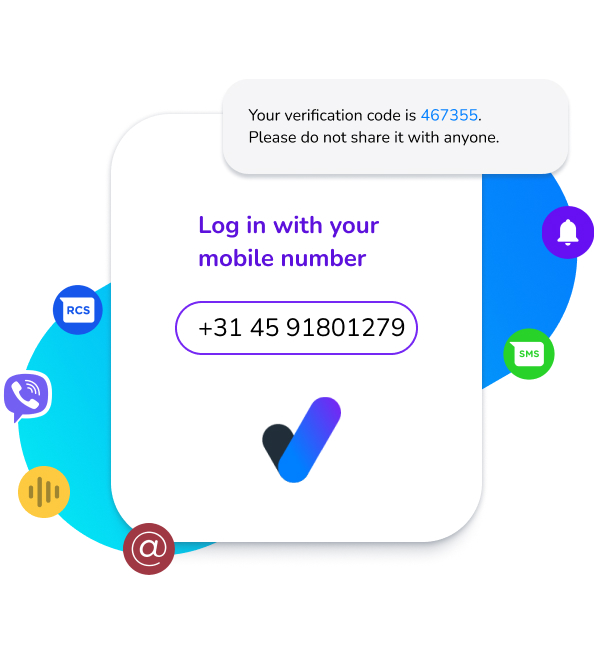
Choose the best verification channel with the right level of security.
Use the latest verification methods and make logins and authentications seamless.
Protect your customers and your business with fraud traffic monitoring.
Choose the most cost-effective authentication methods and tailor them to your needs.
Confirm the access rights of your customers to your online services by authentication via preferred channels. Choose the right messaging channels for your audience and improve the customer experience.
Speak to an expertDouble-check users with the help of mobile identity services, SIM card information and ID checks and scans to confirm users are who they say they are. This includes online verifications, age verifications and logins.
ID Scan: scan passports and other IDs with a mobile phone.
Mobile Identity Services: leverage the power of the SIM card.
iDIN: identify customers for direct login (Dutch customers only)
Protect your messaging traffic 24/7/365 from any fraudulent activity with our Safeguard software. Its features include AI Anomaly Detection, Destination Management, Account/Recipient Limits and Alerts.
What is Safeguard?Onboard and grant access to users in a smooth and secure manner
Protect data or transactions from fraudsters
Monitor logins and accounts to prevent unauthorised access
Double-check and verify users by confirming mobile numbers
Set up traffic rules and monitoring to detect and prevent fraud
One API, multiple OTP channels. Choose the perfect channels for your audience and improve the user experience.
One API for the most secure and user friendly verification services including OTPs and Number Verify. Only pay per successful verification.
Build and configure your own tailored verification and security solution with nine available channels to perfectly fit existing processes.
With cybercrime on the rise, it's more important than ever to secure your online data and customers - if you don't want to become the next security breach headline. Safeguard your business and your customers by authenticating users, verifying identities and managing traffic to detect suspicious activities with our CM.com solutions.
Select a region to show relevant information. This may change the language.